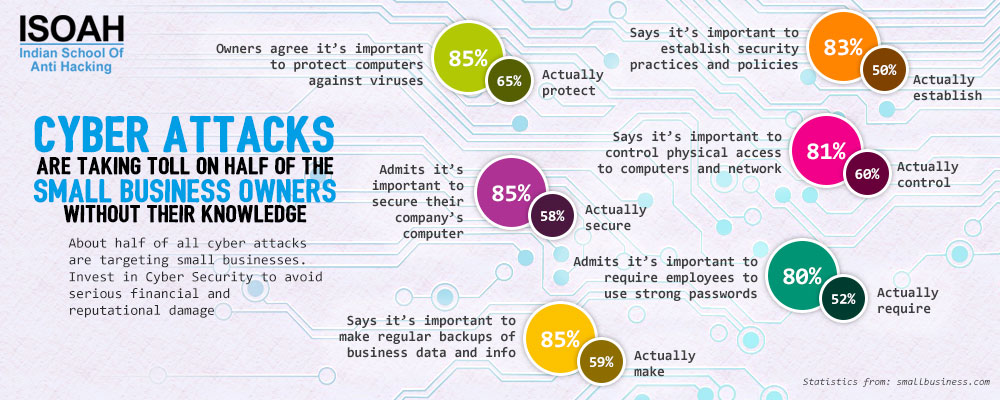
Social media accounts are acting as gold mines for cyber criminals
Article: Cyber Security

Do you think twice before posting the details of your trip or your workplace on social media? No?
Then beware, you might become the potential target of hackers and cyber criminals.
According to Cyber crime experts and forensic consultants, hackers scour through social media database of employees of organizations they intend to attack and send phishing mails to them. It is anticipated that advanced attacks against social media networks will be able to leverage a user's contacts, locations, and even business activities. A recent report by EY on Cybercrime Incidents in India highlighted how social media was emerging as one of the biggest risk zones from the perspective of cyber attacks, with 90% of the 160 top executives responding to the survey identifying it as a major source of cyber attacks.
Social media sites generate revenue from targeted advertising that is personalized for each user based on their interest, location, demographics etc. That's why they encourage the users to share as much information as possible. More engagement means more value is being added to the social network and its advertisers.
Before we proceed to know how social media can become a potential tool for cyber criminals, let's have a look at the things that we should not ever share publicly.
- The exact details of your upcoming vacation
- Videos of your friends that you took without permission
- Inappropriate personal images
- Bank or credit card information
- Complaints about your boss
- Strong political opinion
- Fight with your dear ones
- Selfies in serious or sacred places
- Unsubstantiated accusations
Cybercrime on social networks can happen in many ways.
- The traditional broad-sweep scams lure the user to click on something or visit pages that will push malware into the computer.
- Social media is used as a platform to connect, exchange ideas and trade stolen information.
- Your personal data can be carelessly exposed in public.
Excessive usage of social media by anyone with low awareness can increase the risk of cyber attack. In organizations as well, employees who constantly post their day-to-day happenings related to work on social media could be weak links in the organization and vulnerable to hacks. With the increased speed of digitization of payments and technology at financial institutions, the threat of cyber attacks has grown manifold times.
So, what are the threats?
1. Identity theft & exploiting them:
In the age of digitalization, nothing is more important than information. Millions of online users use their personal information in order to get registered with one or more social media platforms. Such huge information with personal data of so many people is one of the easiest targets for many cyber criminals. Information about the user's date of birth, relationship status, location, schools attended and place of work is often displayed. By further researching connections and posts, it is easy to figure out family relationships, friend circles, main interests, hobbies and much more. With a little bit of research, they can easily retrieve information to crack through the security questions, impersonate the victim, gain access to victim's banking and e-commerce accounts and execute fraudulent actions.
2. Phishing attacks through social media:
On social media, nobody can be trusted. But we hardly doubt links that are sent through social media by our friends. There are signs to recognize a suspicious link. There are things like drive-by-downloads, infected adverts through which your machines can be compromised. In many cases, the initial malware is just a gateway into the system. It doesn't do any harm but once a backdoor is established on the infected computer, that access may be put up for sale. Once the criminals receive the access of the computer, criminals install software which can hijack the victim's online banking credentials, read username and passwords. In social media, we often come across third-party apps that demand the permission to check your contacts, messages, profile pictures etc. They are meant to extract your personal data that are useful for cyber criminals in a variety of ways.
3. Monetizing information available on social media
Cyber criminals try to monetize information available on social networks by targeting payment information that may be stored in user profiles. Attackers use the login credentials of a compromised account that can be gained through phishing, malware attacks or malicious social apps. Payment settings on these sites allow users to initiate in-app purchases directly from social media apps and games. Payment settings are also needed to purchase social network advertising. Payment settings are enabled in most of the user accounts and hackers know that. If an attacker gains full control over a victim's social media account, a malicious app can be installed and such application can forcefully create in-app purchases directing the money to attacker's account.
4. Exploiting the trust of the consumers for personal gain
Engaging with the consumers through various online platforms has become the norm for driving more business and building trust. Social media plays an important part when it comes to building a trusted relationship with the consumers and attackers know that. Compromising trusted fan pages enables cybercriminals to reach hundreds and thousands of consumers at once and it becomes easy for them to lure consumers to phishing sites, where they will be asked to submit their credentials. Another option is to lure consumers to access exploit sites or convince visitors to download malware to their endpoints. A compromised endpoint infected with advanced malware allows the attacker to not only gain further access to information on the endpoint itself but can also open up a variety of potential cybercrime vectors that enable attackers to offer their botnet for distributed denial-of-service activities or proxies addresses.
Thus social media is becoming an ideal hunting ground for anyone who has a clear target to attack, be it an individual or organization, and damage the reputation or can cause huge financial loss. We can minimize the threat of cyber attack or cyber crime by getting a little aware and conscious while using social media platforms. There is no magic or a single piece of software that can protect us. It's a cat and mouse game where the bad guys (black-hat hackers) are trying to attack and the good guys (white hack hackers) are trying to defend.